There are many articles about completely clearing Firefox’s form auto-complete history. However, I’ve often mistyped something into a form and then either had to live with those typos always showing up or lose my complete form history by clearing it. There is a better way!
Although you can’t easily edit or modify the characters that are stored, you can remove individual items in the form history with just a few keystrokes.
- Go to the form that has the field with the auto-complete history entry that you want to delete
- Type the first few characters of the value you want to remove. You’ll see the value appear in the drop down list below the form field as usual. In this example, I want to remove the misspelled entry, “knwoledge”.
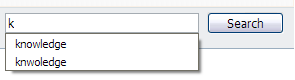
- Use the down-arrow key to highlight the history item to be deleted. Don’t click it with the mouse.
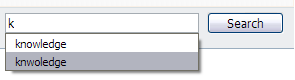
- Press the Delete (Del) key, instead of Enter, and the item will be gone
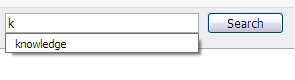
Yea! No more garbage in your form auto-complete history.
This method is also useful for security and privacy purposes to selectively remove data, such as credit card, Social Security, bank account and other identification numbers, that you don’t want lying around in Firefox’s form history.
Update: From the comments, use Shift+Delete on Mac OS X.

 I was recently asked how to password protect a USB memory stick (a.k.a. thumb drive, USB key, etc.) without having to buy software.
I was recently asked how to password protect a USB memory stick (a.k.a. thumb drive, USB key, etc.) without having to buy software.